If you’re curious about what all the hubbub is regarding PCI DSS and who it applies to and why, you’ve come to the right place. This post is dedicated to this ubiquitous standard and all of the benefits of adhering to it!
While this article isn’t intended to be an exhaustive guide to every iota of your business’s journey to PCI compliance, we have done our best to assemble some of the most frequently asked questions (and answers to those questions!) in one place for your convenient reference.
Skip to the good stuff:
- What is PCI DSS
- Who does PCI DSS apply to?
- Does my business have to be PCI compliant?
- How can I become PCI compliant?
- What if I use third-party services and plugins?
- How is PCI compliance evaluated?
- What happens when I am PCI compliant?
What is PCI DSS?
PCI DSS is an unwieldy acronym that stands for Payment Card Industry Data Security Standard.
It represents a collection of regulations that the big card companies invented in the mid-2000s in order to better protect consumer card information from breaches and fraud.
Who does PCI DSS apply to?
There’s a lot of blogs and other content out there describing who PCI does and doesn’t apply to, but we think WooCommerce’s official documentation says it best:
“If you store, process, or transmit cardholder data (as defined in the PCI Security Standards Council’s glossary), yes [it applies to you].
If, however, you are taking payments off-site by using a gateway that uses its own servers to take payments (Stripe, PayPal Payments, etc.) and you are not collecting, transmitting, or processing cardholder data, PCI-DSS is not applicable to you.”
Does my business have to be PCI compliant?
The PCI website says it best: “following PCI DSS is just good business”, and we agree with that 100%.
Information about payment cards and account owners will always be a priority target for malicious parties, and WordPress is by far the most popular CMS for hackers. This means your eCommerce site is at ever-present risk of being breached even if you don’t process cardholder data.
The good news is that eCommerce sites often have a smaller attack surface than big chains of brick-and-mortar stores because their payment systems are typically less complex (no physical card scanners, no POS systems, etc.).
PCI is not a law, so you won’t go to jail if your business is not compliant. That said, the PCI standard was created by Visa, MasterCard, Discover, AMEX, and JCB for good reason – to keep consumers and businesses safe.
Accepting or processing their organizations’ payment cards is a great boon for many companies, and business owners are expected to do their due diligence in order to be able to benefit from these systems.
Non-compliant businesses can face anything from fines to penalties or even be barred from accepting credit card payments altogether.

These fines and penalties aren’t slaps on the wrist, either. If a non-compliant business falls prey to a data breach, these payment brands can pass on fines of up to $100,000 per month to your acquiring bank, which is almost guaranteed to pass that on to you!
Running a non-compliant business is like driving your own taxi without car insurance. Even if you are T-boned by someone else, you’ll be the one slapped with the big fines and forced to pay out of pocket just to get back on the road. That’s assuming you’re still allowed to drive and your car can be fixed.
Worse still, your reputation will suffer when your customers figure out that you did not prioritize your (and their!) safety. An excellent blog post by Sucuri found that 57% of customers lose their trust in an organization that has experienced a data breach, and just under a third take their business elsewhere for good.
So do you have to be compliant? According to the law, no. Should you be compliant? According to responsible business practices, yes.
How can I become PCI compliant?
The complexity of your journey to PCI compliance depends on the variety and number of system components within your cardholder data environment. In plain English, it means that the more people, processes, and technology that you have handling cardholder or authentication data, the stricter the requirements for compliance.
PCI has great resources available for business owners on its site, and we recommend starting there if you’re looking to do some reading yourself first.
Right off the bat, we can share that there’s a very high likelihood that eCommerce site owners will have to fill out a Self-Assessment Questionnaire (SAQ) at some stage of your journey, and all of PCI’s SAQs are available on their website to help you familiarize yourself with compliance requirements.
(Or, you can skip to the overview a bit farther down in this article).
Sooner or later, though, you’ll want to turn to outside help by contacting either your merchant bank or compliance specialist. As opposed to me, some guy in a ninja outfit writing about financial practices on the internet, your bank or specialist will be fully equipped to guide you throughout your business-specific process of becoming compliant.
What if I use third-party services and plugins?
It depends.
Popular services such as WooCommerce, PayPal, and Stripe have their own obligations in regards to PCI compliance, and each of these providers have their own documentation available online for your reference.
However, please keep in mind that using any of these services does not automatically remove the burden of compliance from your business.
Your PCI requirements depend on the structure of your eCommerce store and network. Again, we recommend reaching out to your merchant bank and/or payment provider in order to clarify your circumstances.
How is PCI compliance evaluated?
PCI compliance is evaluated using 12 “Goals” that all correspond to different aspects of effective informational security.
You can check out the official PCI Quick Guide here.
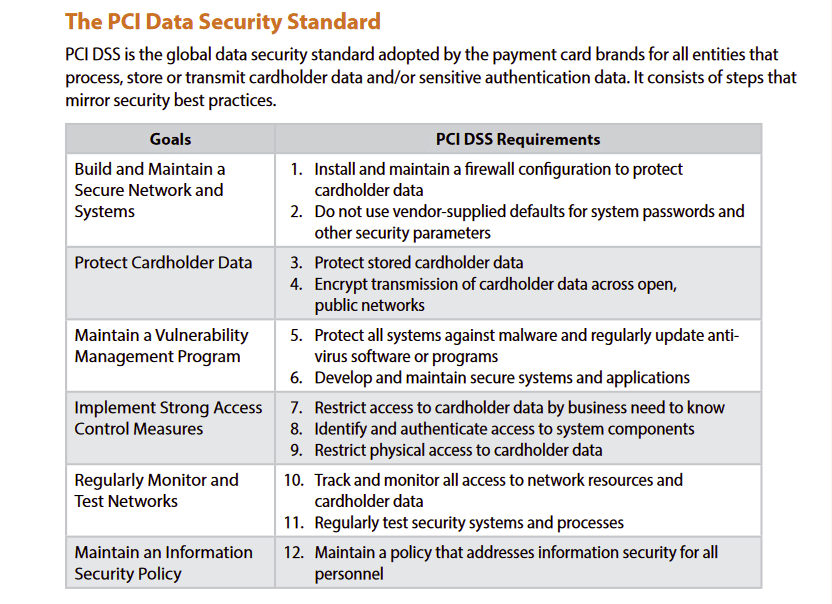
The Quick Guide does an excellent job of unpacking these requirements (and sub-requirements) in detail.
If you own an SMB and your jaw has dropped while reading this list, we’d encourage you not to worry. There’s a lot of technical language being thrown around, but addressing these requirements isn’t as intimidating as it may look.
Melapress wrote a particularly good (and somewhat technical) article covering how a business owner can approach fulfilling these PCI requirements, and we encourage you to check it out as well.
We’re going to stick to an age-old format: TL;DRs, our recommendations, and memes.
Requirement 1 – Install and maintain a firewall configuration to protect cardholder data
Short Version: Any connection between your cardholder data environment (CDE) and other networks should have a properly configured firewall on it.
Recommendations: There is no shortage of quality WordPress firewalls, and we compared two great options – WordFence and Sucuri.
Do make sure that your firewall is properly configured. Also, any machines that have CDE access and can connect to the Internet when outside of your network (e.g. employee laptops) should have personal firewalls on them.

Be sure to thoroughly document every aspect of your firewall setup. Also, we’re giving you fair warning now – good documentation is a significant aspect of every single requirement, so prepare yourself now for a flurry of record-keeping.
For example, Requirement 1 expects you to keep track of things such as: servers, network devices, services that interact with your website, and your firewall configurations.
Requirement 2 – Do not use vendor-supplied defaults for system passwords and other security parameters.
Short Version: Change default passwords and update hardware/software in a timely manner.
Recommendations: Even the free versions of security plugins like WordFence and Sucuri have functionalities that remind you to change weak passwords and notify you when you need to update, and we can’t stress how vital it is to remove these default passwords.
The popularity of WordPress and the pervasiveness of passwords like “pass” or “admin” or “[none]” encourage WordPress hackers to travel the path of least resistance, and they often do so with great success.

Hackers that can’t get into your cPanel or admin account because it’s locked behind a strong password are more likely to pivot to another website than invest time and resources into trying to brute force their way in.
Even if they do try to brute force their way in, a properly configured security setup will lock suspicious IP addresses out of your site and alert you of the attempt, which puts you in a position to take further defensive action.
Minimizing your attack surface is also a key element of good password management. Get rid of plugins you don’t use. Don’t add features that you don’t need, like the bonus email server your web host is offering for free with your plan.
Every login portal and account is just another door that hackers can break into.
Finally, diversify your processes wherever possible. One organization should not hold the keys to your domain, DNS nameservers, web host, staging site, live site, and email services.
Requirement 3 – protect stored cardholder data
Short Version: Don’t record data you don’t need, protect the data you do need, and delete records when they’re not relevant anymore.
Recommendations: Wherever possible, reduce the amount of cardholder data stored in your environment. If you have access to any amount of cardholder data, it has to be properly encrypted.
PCI’s breakdown of what can and cannot be stored below.
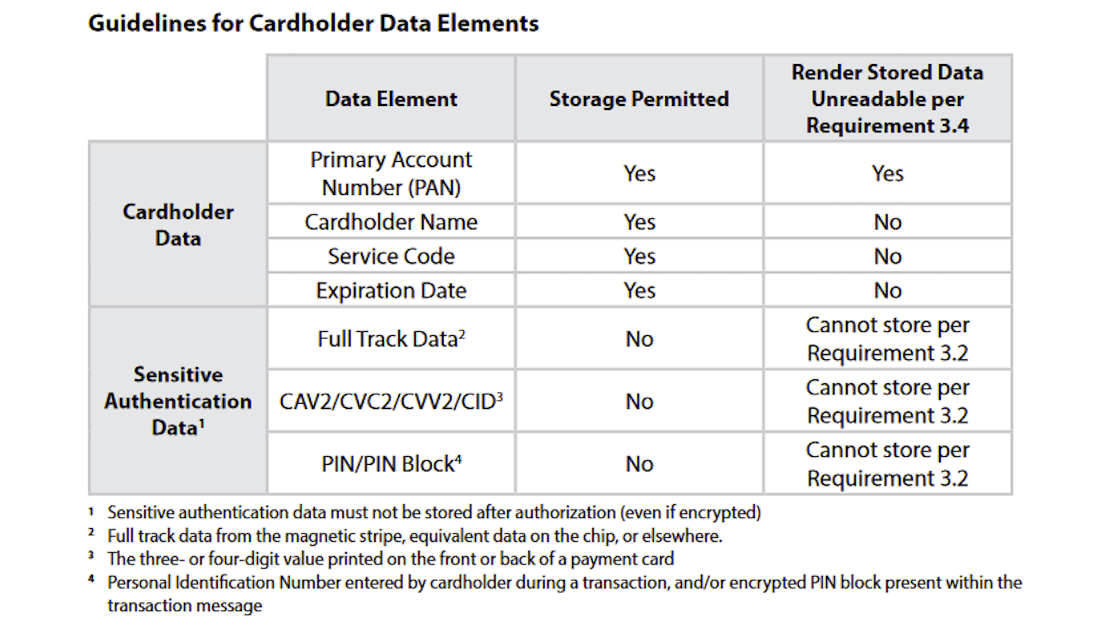
Bear in mind that many eCommerce sites choose to employ third party service providers for exactly this reason, so you may not be storing cardholder data at all.
Everything depends on your shopping cart configuration, and you can find a chart outlining the levels of complexity and risk involved with various configurations below.
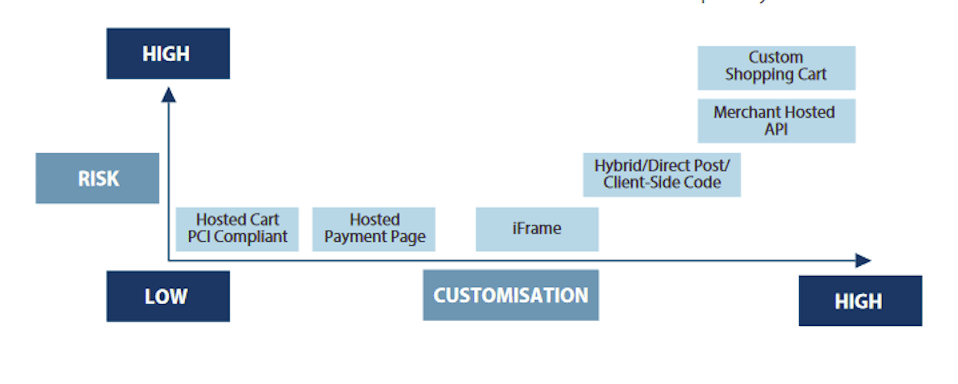
Requirement 4 – Encrypt transmission of cardholder data across open, public networks
Short Version: Purchase a security certificate for your site and don’t log into your payment accounts using coffee shop WiFi.
Recommendations: There’s really not much to add here. Installing and adding a security certificate allows your site to be accessible over HTTPS, which means all traffic between your users and your site is encrypted.

Any and all traffic that involves cardholder data should also be as secure as possible. Avoid public WiFi networks unless you have a good VPN and never allow any cardholder information to be passed along unencrypted channels.
Requirement 5 – protect all systems against malware and regularly update anti-virus software or programs
Short Version: Use an antivirus that is configured correctly and updated consistently.
Recommendations: If you have installed a WordPress security plugin such as WordFence or Sucuri, chances are that it will have a malware scanner built in.
A scanner will help keep your environment safe from malicious software that exploits known system vulnerabilities, and it’s an essential component of your information security setup.

The malware that remains undetected is the malware that can hang out on servers for months (or years) and destroy your business. Scan comprehensively and scan often.
Requirement 6 – develop and maintain secure systems and applications
Short Version: Keep everything properly patched and don’t download applications or software from unreliable sources.
Recommendations: This requirement is a bit of a hodge-podge of making sure new stuff’s safe, keeping your current stuff safe, and developing safe stuff. We’re going to gloss over the parts of this requirement that apply to developers, though.
As far as maintaining your current systems goes, you should only use properly licensed products developed by reliable, responsive vendors. These vendors will issue updates and/or patches to their products to address vulnerabilities from time to time, and you should implement these updates as soon as possible.
Safely acquiring new products mostly boils down to doing your research when shopping for applications or other software.

Are there existing user reviews for the product? Is the product available through official, secure channels? Is there a visible history of patches or updates?
Trust your gut and avoid things that seem sketchy – chances are, they are.
Requirement 7 – restrict access to cardholder data by business need-to-know
Short Version: Keep access restricted to people who need it.
Recommendations: The Principle of Least Privilege, or the idea of not giving users more access than what they need to do their specific tasks, is a great security baseline for any organization.
WordPress has several available roles by default for a reason, and that reason is access control. There’s no reason to hand out high-level access to someone in order to slightly simplify a job or provide temporary access to some sort of information.
Even if one of your users or site managers requires a resource that’s “outside of their lane”, creating an extra set of admin-level credentials is rarely the best way to approach the problem.

This extends beyond just WordPress though. The Principle of Least Privilege can be applied to every aspect of your environment, including your hosting, network, firewalls, and much more.
Requirement 8 – identify and authenticate access to system components
Short Version: Use 2FA, make sure everyone with access to your site has unique credentials, and encourage your users to use strong passwords.
Recommendations: Again, this is a lot of technical language for what basically boils down to making sure everyone has their own login credentials and strong passwords.
2-Factor Authentication is one of the best ways to keep your site safe from brute force attacks, and there are several third-party plugins that business owners can consider.
Installing an activity log on your WordPress installation is also recommended. Activity logs by themselves allow you to keep track of even the smallest changes to your site.
Employing unique credentials in conjunction with an activity log means you have a record of each user’s activity on your site, giving you early warning awareness of any unusual activity.

Finally, while the password to your admin account is obviously the golden egg most hackers are after, a lot of damage can be done with user account credentials as well.
The last thing you want to hear from your users is that their accounts on your website have been hijacked.
Requirement 9 – restrict physical access to cardholder data
Short Version: Don’t give physical access to your servers, laptops, computers, smartphones, etc. to people who don’t need access.
Recommendations: This one is much more applicable to brick-and-mortar stores, but there are elements for eCommerce here as well.
Make sure your devices have locks or passwords to keep them safe from physical attempts at entry, and always password protect your WiFi networks.
This one’s almost too short to turn into a proper meme.
…almost.
Requirement 10 – track and monitor all access to network resources and cardholder data
Short Version: enable logs on every device/installation that you can, keep logs for a minimum of one year, the last 90 days of activity logs must be instantly available upon request
Recommendations: We’ve already touched on the importance of keeping logs wherever you can, but it’s also worth mentioning that your network devices (switches, routers) and network services (SMTP, web server) can keep logs too. Enable this functionality wherever you can.
The type of logs and information that have to be kept are many, and we highly recommend reviewing the Quick Guide in order to get acquainted with PCI’s requirements (specifically, 10.1 – 10.4).
There are also several other simple things to keep track of here, such as making sure all of your records are synced chronologically, reviewing logs regularly, and having detection and reporting procedures in place.

Requirement 11 – regularly test security systems and processes
Short Version: Run consistent tests on your security setup to make sure there are no obvious issues with it and set up an Intrusion Detection System (IDS) or Intrusion Protection System (IPS).
Recommendations: There are many types of scans and tests included in this requirement intended to validate (or not validate) the integrity of your environment at the network level and internally.
Security is a living, breathing part of your site that must be updated and verified in order to be effective, and that’s because the rest of your site is composed of parts that also live and breathe.
As different parts of your website evolve, so too does the long list of known exploits and vulnerabilities hackers can easily reference in order to breach WordPress websites.
That’s why audits, network scans, vulnerability scans, and penetration tests should be carried out with varying frequency (and after big updates) by both you and Approved Scanning Vendors (ASVs) to make sure there are no holes in your site’s proverbial armor.
Fortunately, many WordPress security plugins also come with an IDS or IPS built-in, so you probably won’t have to seek out a separate solution in order to fulfill this specific requirement (11.4).
Requirement 12 – maintain a policy that addresses information security for all personnel
Short Version: Have a document dedicated to the ins and outs of your security setup and lay out an incident response (IR) plan.
Recommendations: This relatively labor-intensive requirement is more relevant to larger companies with distinct departments or teams that would have to coordinate in order to document the many processes outlined here.
That said, after going through all the paperwork and fuss of making your business compliant, why wouldn’t you want to have a set of documents in place that address things like: overall security policy, past vulnerabilities, how to configure your network devices correctly, who’s in charge of checking the logs, etc.?
Producing the first drafts of these policies is no small feat, particularly for SME, but there are several applicable use cases to consider:
- If your business expanded and you hired new employees to help maintain your site, what documents would serve as their baseline?
- If you needed to get outside development/auditing help, what materials would you share to provide an overview of your security setup (as opposed to having them use billable hours to map everything out themselves)?
- If you were to identify a major breach on your site, what procedures would you follow?
Having everything down on paper doesn’t only provide you with an outline of how to keep your business safe and compliant, it massively streamlines the process of documenting updates to your site and security setup as your business grows over time.
If it seems like we’re making a mountain out of a molehill, consider the following:
The good folks over at Sucuri found that a third of companies have no plans for handling (or even looking for) vulnerabilities on their websites, which means their sites could fall prey to widely known exploits at any time.
Even more concerning is the reality that these companies have no game plan for when the worst does happen.
Don’t be like those companies.
What happens when I am PCI compliant?
Great! You’ve done the paperwork and are now PCI compliant. What does it actually do for you and your business, though?
Reduces Risk of Data Breaches
The steps outlined by PCI harden your business considerably against cyber threats. It’s impossible to bring the threat level down to zero, but that’s no excuse for not taking every reasonable measure possible to protect your assets.
It bears repeating that many WordPress hackers do their best to walk the path of least resistance, as poorly defended sites can be compromised by hackers in as little as under 10 minutes.
Implementing the controls and procedures outlined by PCI DSS will make getting into your site and accessing cardholder data considerably more difficult, increasing the chances that bad actors will just throw up their arms and move on to find an easier target.
Helps You Avoid Fines / Reduces Cost of Data Breach
Question 26 of the PCI FAQ states the following:
“At their acquirers’/service providers’ discretion, merchants that do not comply with PCI DSS may be subject to fines, card replacement costs, costly forensic audits, brand damage, etc., should a breach event occur.”
We’ve already discussed the scale of fines that non-compliant businesses can be slapped with earlier in this article (up to $100,000 a month), but that was just the tip of the iceberg.
Card replacement costs can come in at anything from $2-5 per card, and breaches for big businesses can result in the loss of tens of millions of card numbers. You can do the math on that one.
SMB is obviously working on a different scale, but all it takes is one breach to steal thousands or tens of thousands of card numbers from an unsecure system.
Obviously, not being subject to all of these things is a much more desirable outcome for your wallet, and that’s where PCI compliance comes in.
Local laws vary, but some states even shield PCI-compliant entities from liability in the event of a breach.
In other words, it pays to be safe, and it pays well.
Protects Your Customers
People nowadays want to be able to purchase two hundred pairs of woolen socks from the comfort of their home on a whim, and tapping into that convenience is part of the magic of eCommerce.
Consumers who shop online want to feel like they can do so safely, so providing a secure environment in which people can spend their money simply makes sense.
Improves Your Brand’s Reputation
Showing the world that you are PCI compliant is proof that you take your business seriously and everyone from your competitors to customers to potential partners will see the value in this.
Unified International Standard
PCI DSS is a globally accepted standard that’s not tied to the legislation of any one country. This means you don’t have to necessarily bog yourself down by adjusting your data environment to the security requirements of every single state or country your users come from.
However, again, we’re not lawyers. Reach out to your merchant bank or compliance specialist with questions about your business’s journey to compliance so you don’t wind up like Facebook Meta.
Encourages Security-Focused Mindset
One of the best old-time sayings that apply to this situation is “an ounce of prevention is worth a pound of cure”.
Maintaining a security-focused approach keeps you safer and smarter, and it’s certainly easier to manage once you have everything in place and documented.
It also keeps you richer. Unfortunately, security remains a back-burner issue for many site owners, something that’s not worth thinking about until it materializes in the form of financial ruin.

It’s never too early to start thinking about how to keep your site safe, so why not start now (if you haven’t already)?
Provides a Baseline for Other Regulations
Many of the basic premises of PCI DSS dovetail well with standards such as GDPR, ISO and other internationally-mandated data security regulations, reducing the amount of total work and resources that you (the busy business owner) have to invest into them.
Peace of Mind
Putting any information about yourself online presents a risk, and your customers are sure to appreciate the peace of mind that comes with knowing their card details aren’t stored in an unencrypted text file in your databases. (No, I’m not joking – remember the TalkTalk cyber attacks?
You can also rest easy knowing that there is a sophisticated array of defenses standing between you and the bad guys.
That means you can focus on what matters – building an even stronger and more successful eCommerce experience for your user base. Or a side project. Or walking your dog an extra time every day. The choice is yours!
PCI DSS: The Bottom line
Becoming PCI compliant is one of the best things you can do, both for the sake of your business and your customers. If you have any additional questions, make sure to drop a comment below! You can also get assistance to optimize your online store from our e-commerce experts.


